Network Security Best Practices
Risk Analysis
You should have some
kind of risk analysis done to determine as near as possible the risk you face with the kind of operation you
conduct.
Vulnerability Testing
Your security policy
should include regular vulnerability testing
to determine system. For known security weaknesses
Audits
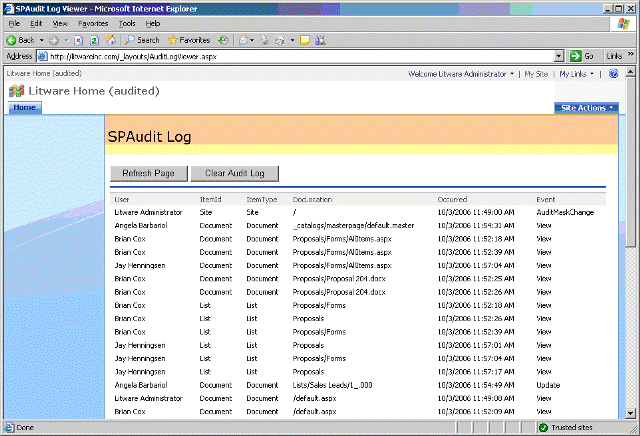
*Audit logs that can track user authentication attempts.
*Audit record logs
that are second common type of security related operating system logs.
Audit logs
Tools of your Trade
* Anti spyware
* Anti spam
* Penetration shielding
* Threat signature
recognition
Anti spyware
Anti spam
Penetration shielding
Firewalls





Walang komento:
Mag-post ng isang Komento